Securing Your Microsoft 365 Backups with Cloud Encryption
Microsoft 365 is a widely used cloud platform for communication and collaboration. Office 365 user data can include sensitive information, which is why it is important to protect it against data breaches and leaks.
Office 365 encryption is used to protect user data in the Microsoft cloud and when communicating with Microsoft servers. This blog post explains Microsoft 365 encryption and its different use cases, including how to configure encryption for Microsoft 365 backups.
What Is Office 365 Encryption?
Encryption is a security mechanism for data that works by transforming it from a readable format, known as plaintext, into an unreadable format, known as ciphertext. This data transformation is achieved using an encryption algorithm and an encryption key. The key is a specific piece of information that determines how the data is scrambled. Only users with the right decryption key can reverse the process, converting the ciphertext back into its original plaintext form.
The encryption process begins with plaintext, which is the original, readable data. When encryption is applied, the algorithm uses the encryption key to convert this plaintext into ciphertext. This ciphertext is generated as a random combination of characters and is not understandable without the corresponding decryption key. The strength of encryption depends on several factors, including the complexity of the algorithm and the length of the key, with longer keys generally providing stronger encryption.
In Microsoft 365, encryption plays a critical role in safeguarding data, especially in the cloud environment where data is often stored, processed, and transmitted across the internet. When data is encrypted, even if unauthorized individuals or malicious actors intercept it, they cannot read or misuse it without the decryption key. This is crucial to protecting sensitive information such as emails, documents, and personal data against leaks and breaches.
Encryption is important in Microsoft 365 and in the cloud because it provides a strong layer of security and ensures data privacy and compliance with regulations. It helps organizations protect their sensitive information, adhere to legal requirements related to data protection, and maintain customer trust.
How Does Encryption Work in Microsoft 365?
The encryption process within Microsoft 365 occurs at various stages:
- When data is transmitted from a user’s device to Microsoft cloud servers, it is encrypted in transit as it travels over the internet using protocols like TLS (Transport Layer Security). This ensures that any data intercepted during transmission remains secure.
- Once the data arrives at the Microsoft data centers, it is encrypted at rest using strong encryption algorithms like AES-256. This means that even if the physical storage where the data resides is compromised, the data itself remains protected.
- Data at rest, such as files stored in Exchange Online mailboxes, OneDrive for Business, and SharePoint Online is encrypted using BitLocker, which secures entire disk volumes on the servers.
- Additionally, individual files are encrypted using per-file encryption, using the Azure Storage Service Encryption (SSE) with 256-bit AES encryption, one of the strongest encryption algorithms available.
- Email encryption within Microsoft 365, particularly in Exchange Online, is managed through Office Message Encryption (OME). This allows emails to be encrypted and protected using encryption technologies such as S/MIME (Secure/Multipurpose Internet Mail Extensions) and IRM (Information Rights Management), which also enables data access control. You can read more about Microsoft 365 message encryption in our post.
- Additionally, customer-controlled encryption allows organizations to use their own encryption keys, managed through Azure Key Vault, providing an added layer of control and security.
System administrators have various tools and dashboards at their disposal to manage and monitor encryption settings. Admins can use Microsoft 365 Security & Compliance Center and the Microsoft 365 Admin Center to configure encryption policies, manage customer keys, and monitor encryption-related activities across their organization.
Moreover, Microsoft provides regular transparency reports and has compliance certifications to give system administrators assurance that encryption practices align with global standards. These include certifications for ISO 27001, SOC 1, SOC 2, and GDPR compliance.
Microsoft 365 Crypto Update
The introduction of AES-256 CBC (Cipher Block Chaining mode) in Microsoft 365 in 2023 marked a significant enhancement in data encryption. AES-256 is a robust encryption standard, and the use of CBC mode adds an additional layer of complexity and security by chaining each block of ciphertext to the previous one, which helps prevent certain types of cryptographic attacks.
For system administrators, this transition required careful examination of the existing data encryption policies to verify and ensure that their encryption management and monitoring tools could handle the updated encryption standard. Admins needed to confirm that any custom encryption keys or policies were compatible with the new AES-256 CBC mode to avoid potential conflicts or issues.
Microsoft provided documentation and tools to assist in this process, ensuring that admins could maintain compliance and security without significant manual intervention. Microsoft ensured that this change was seamless for most users, with minimal impact on the existing configuration. The update was rolled out in a way that existing data was re-encrypted using AES-256 CBC without disrupting access or functionality of Microsoft 365.
Applications of Microsoft Office 2013, 2016, 2019 and 2021 should be reconfigured to use the AES256-CBC mode by using group policies in Windows or cloud policies in Microsoft 365. Since Microsoft 365 apps version 16.0.16327, the AES256-CBC mode is used by default.
If Microsoft Exchange Server is used, then administrators should install a hotfix. If the Azure Rights Management Connector Service is used with Exchange Server, then it is recommended that administrators run the GenConnectorConfig.ps1 script provided by Microsoft on each Exchange server.
Encryption for Data at Rest and in Transit
Encryption for data at rest and in transit is a fundamental security measure in Microsoft 365, with the purpose of protecting sensitive information from unauthorized access and breaches. Let’s break down how encryption is applied in both scenarios within the Microsoft 365 environment.
Data at Rest
Data at rest is information stored on a physical medium, such as a hard drive or a cloud storage service, and is not actively being transmitted across networks. In Microsoft 365, data at rest is encrypted to ensure that even if the physical storage is compromised, the data remains protected.
Examples of data encryption at rest in Microsoft 365 include:
- Files on SharePoint and OneDrive. When users store files in SharePoint Online or OneDrive for Business, these files are encrypted using Azure Storage Service Encryption (SSE). Microsoft 365 uses AES-256, a strong encryption standard, to encrypt each file and ensure that it remains secure on the server. Additionally, BitLocker is used to encrypt the entire disk where the data resides, providing an extra layer of protection.
- Email messages in Exchange Online. Emails stored in Exchange Online mailboxes are encrypted using a combination of BitLocker and per-file encryption with AES-256. This means that the entire mailbox database is encrypted, and each email message is also individually encrypted, ensuring that stored emails are secure.
Data in Transit
Data in transit refers to information that is actively being transmitted over a network, such as data being sent between a user’s device and Microsoft servers or between Microsoft data centers. Encryption in transit protects this data from being intercepted or altered during transmission.
Examples of data encryption in transit in Microsoft 365 include:
- Email messages. When emails are sent from one user to another, they are encrypted in transit using Transport Layer Security (TLS). TLS ensures that the email content is protected when this data is transferred across the internet, preventing unauthorized access by interceptors. For additional security, Office Message Encryption (OME) can be applied to emails, enabling encryption that persists even if the email is forwarded outside the organization.
- Online meetings (Microsoft Teams). During online meetings conducted via Microsoft Teams, data such as video, audio and shared files are encrypted in transit using TLS and Secure Real-time Transport Protocol (SRTP). These protocols ensure that all communications during a meeting are secure from eavesdropping or tampering.
Preparing for Cloud Backup Encryption
Microsoft 365 data is strongly encrypted in the Microsoft cloud, which improves the overall security level, as mentioned before. Microsoft 365 data backup is an important part of a data protection strategy, and it is highly recommended that you back up Microsoft 365 data regularly. The backup data can be transferred via the network and stored in the destination location either encrypted or unencrypted.
Unencrypted backups can be a vulnerability for the entire environment. While Microsoft 365 data is encrypted on Microsoft servers in the cloud and in transit, attackers can breach unencrypted Microsoft 365 backups. Encrypted Microsoft 365 backups are more secure.
NAKIVO Backup & Replication is an enterprise data protection solution that supports backup encryption, including encryption of Microsoft 365 backups. You can encrypt the entire backup repository or enable encryption for each backup job individually.
There are three main scenarios for storing encrypted Microsoft 365 backups in the cloud with the NAKIVO solution:
- Creating a backup repository in an Amazon S3 bucket or similar S3-compatible object storage. A Transporter deployed in Amazon Web Services (AWS) is used for communication with a Director and data transferring to the S3 backup repository.
- Creating a backup repository in an EC2 instance. In this case, you can deploy the full solution of NAKIVO Backup & Replication in an Amazon EC2 instance, which is a virtual machine (VM) in AWS. Alternatively, you can deploy an EC2 instance with the Transporter and backup repository to store encrypted backups in the AWS cloud while the Director is deployed on-premises and has a network connection with the Transporter in AWS. It is recommended that you deploy a Linux Transporter for immutability support.
- Deploying a full solution of NAKIVO Backup & Replication with a backup repository on a virtual machine in an Azure cloud or other public cloud.
Let’s look at how to store encrypted Microsoft 365 backups in Amazon S3. In one of our previous blog posts, we covered how to configure Microsoft 365 backups to Amazon S3 in detail using SharePoint Online data for the walkthrough. The workflow to create encrypted Microsoft 365 backups in Amazon S3 includes the same configuration steps except for the last step (Options) to enable encryption. Refer to this post to configure the environment for a backup to Amazon S3. In this blog post, we focus on configuring Microsoft 365 backup encryption and we only briefly cover the preliminary steps.
Preparing for an Encrypted Microsoft 365 Backup to Amazon S3
Perform the required preparation steps if you have not done these steps before:
- Create a bucket in Amazon S3 to be used as a backup repository in the AWS cloud. Enable object versioning and Amazon S3 object lock for the bucket to be able to use backup immutability in NAKIVO Backup & Replication for the recovery points sent to this bucket.
To enable S3 object lock, select your bucket, go to the Properties tab and in the Object Lock section, click Edit. Select Enable, read the warning, confirm that you are acknowledged and hit Save Changes.

- Add AWS to the NAKIVO inventory. You must have an AWS account and generate AWS access keys.
- Add Microsoft 365 to the inventory. When adding a Microsoft 365 account, you can select all supported Microsoft 365 services to back up or select specific services (for example, Exchange Online and OneDrive for Business).

- Deploy a NAKIVO Transporter in AWS or on a local machine. In this example, we deploy a Transporter in AWS. We select the needed AWS region, instance type, and other settings. The Transporter is used for communication with the Director and transferring the backup data to an Amazon S3 bucket, as well as data recovery from the bucket.
- Create a backup repository in an Amazon S3 bucket. You must select an AWS region and the assigned Transporter that has been deployed in AWS.

The environment is ready to create a Microsoft 365 backup job and store encrypted backups in the Amazon S3 cloud.
Preparing for an Encrypted Microsoft 365 Backup to EC2
If you need to back up Microsoft 365 data and store this data encrypted in the cloud but not in Amazon S3 buckets, consider this alternative approach. For simplicity’s sake, in our example, the full solution of NAKIVO Backup & Replication (Director, Transporter and Backup Repository) is deployed in an EC2 instance.
Depending on your requirements, multiple deployment options are available, such as deploying the NAKIVO Backup & Replication full solution on a VM in Azure or other cloud environments or on a local machine and using a backup repository in a public cloud.
- Deploy NAKIVO Backup & Replication as an EC2 instance from an Amazon Machine Image (AMI). If you use another cloud, install the full solution of NAKIVO Backup & Replication on a VM in the cloud.
- If there is no onboard repository, create a local folder backup repository (on the assigned Transporter) on the VM where the NAKIVO solution is installed.
- Add your Microsoft 365 account to the NAKIVO inventory.
You are ready to create a Microsoft 365 backup job and store encrypted backups in a cloud backup repository.
Creating a Microsoft 365 Encrypted Backup
After configuring the environment, including the NAKIVO inventory, Transporter, and backup repository, you should create a new backup job for Microsoft 365 backup.
- In the web interface of the NAKIVO solution, go to Data Protection, click + and click Backup for Microsoft 365.

- At the first step of the new backup job wizard, select the items to protect. You can select items based on the services previously added to the NAKIVO inventory (Exchange Online, OneDrive, SharePoint, Teams). Let’s back up Microsoft OneDrive and the user’s mailbox in this example.

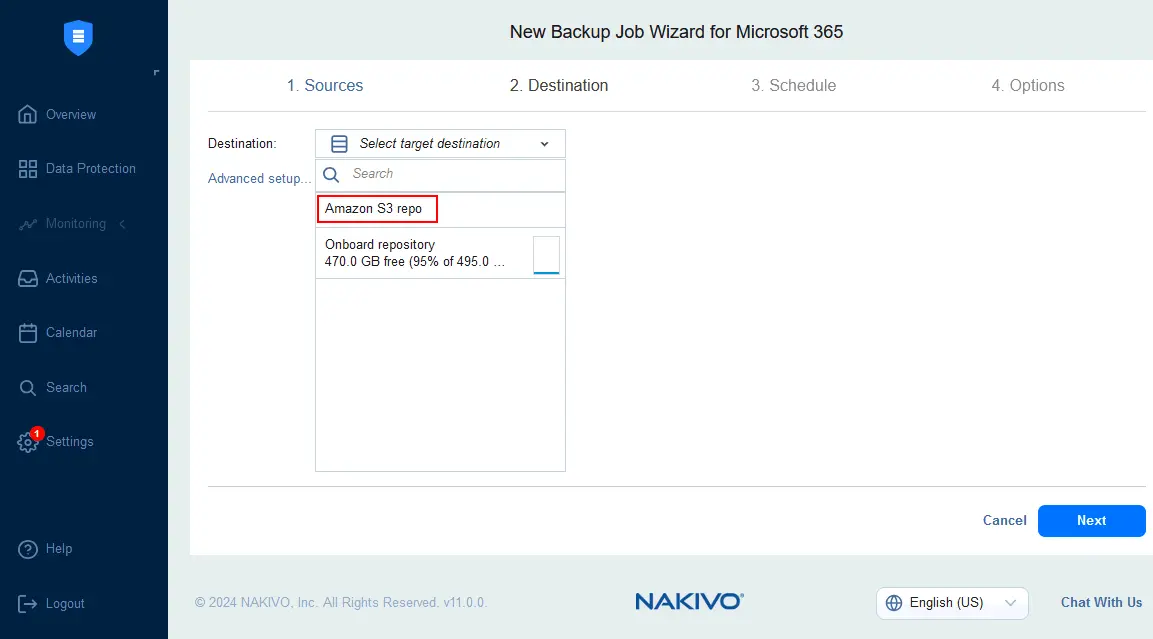
- Select a backup destination. You can select one of the backup repositories added to the NAKIVO solution configuration previously. Select the Amazon S3 repository to store Microsoft 365 recovery points as encrypted data in an Amazon S3 bucket. This is one of the most rational scenarios for storing encrypted Microsoft 365 backups in a public cloud.
- Configure scheduling and retention settings for your Microsoft 365 backup job. You can add multiple schedules, such as daily, weekly, and monthly, as well as implement the GFS retention policy.
Note the immutability checkbox for each schedule. As you recall, we enabled the Amazon S3 Object Lock feature at the beginning of the environment configuration process. Backup immutability significantly improves security together with backup encryption. If ransomware gets access to backup data, it cannot modify, corrupt or delete immutable backup data.

- Configure Microsoft 365 backup job options. At this step, you should set Microsoft 365 backup encryption. Enter a backup job name, for example, Backup Office 365 encryption 01. Set the Backup encryption option as Enabled. Then, click Settings to configure Microsoft 365 backup encryption.
NOTE: If you enable backup encryption, data is encrypted at the source side. The encrypted data is transferred over the network and stored in a backup repository in an encrypted format.

- Set a password for Microsoft 365 backup encryption. You can also select a previously created password in the NAKIVO solution. Enter a password and repeat it. Enter a description for the current password, for example, Microsoft Office 365 encryption for backup.
Alternatively, you can configure a key management service such as AWS Key Management Service (KMS) for backup encryption and to restore the password hash in case you forget it. Hit Proceed.

- A notification message is displayed because we’re not using the Key Management Service in this example when we set backup encryption. Read the notification and make sure to safely store your encryption password. Click Proceed and hit Finish & Run to run the Microsoft 365 backup job with encryption.
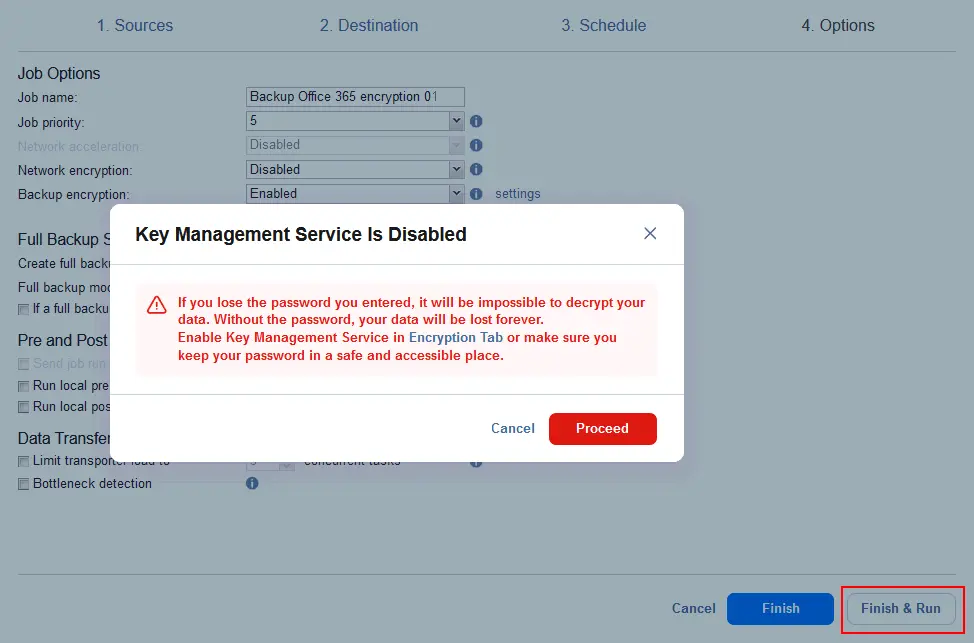
- Check the job scope and schedule to run the backup job right now and click Run.

The alternative approach
If you deploy NAKIVO Backup & Replication (full solution or the Transporter with a backup repository) on a virtual machine in the cloud (AWS, Azure, or another public cloud), the workflow for creating a new Microsoft 365 backup job is different at the step of backup destination selection. To configure an encrypted Microsoft 365 backup job in this scenario, do the following:
- In the web interface of the NAKIVO solution, go to Data Protection, click + and hit Backup for Microsoft 365.
- At the Sources step of the backup wizard, select Office 365 items to back up, such as user emails, OneDrives, SharePoint Sites, Teams, etc.
- At the Destination step, select a backup repository to store the encrypted Microsoft 365 backup. In this example, we select the onboard repository since we use the full solution of NAKIVO Backup & Replication (Director, Transporter, and Backup Repository) installed on a VM in the cloud. Using this configuration, we can store encrypted backups in the cloud.
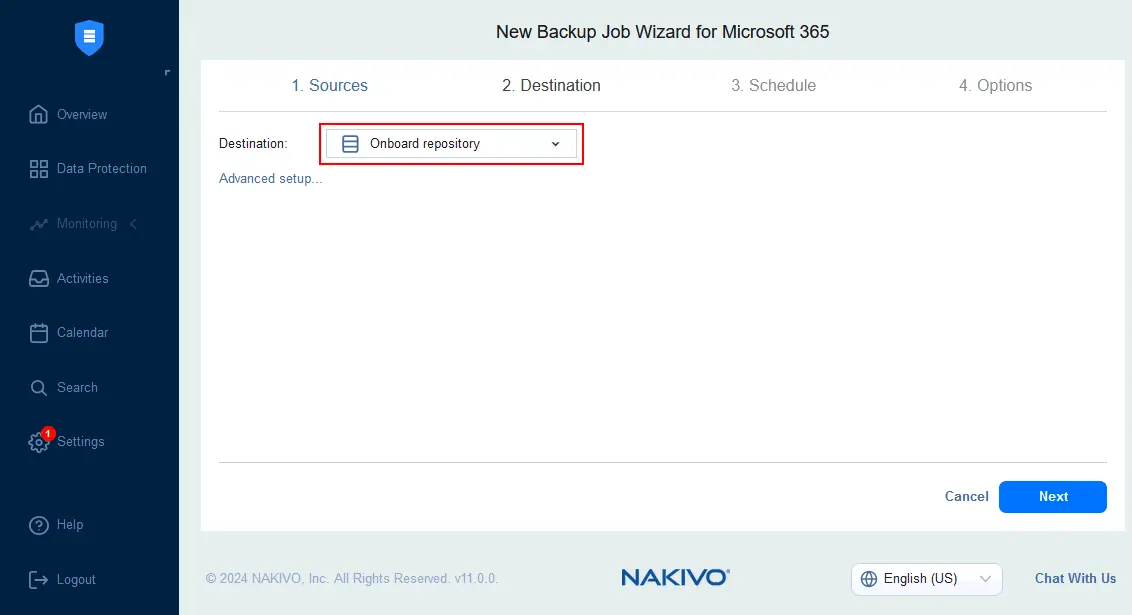
- Configure scheduling and retention settings, as explained in the previous example. It is recommended that you enable backup immutability by selecting the Immutable for checkbox and setting the number of days. Backup immutability is supported for backup repositories assigned to a Linux Transporter.

- Finally, configure Microsoft 365 backup encryption at the Options step of the new backup job wizard. Enter a backup job name to display, for example, Backup Office 365 encryption 02. Select Enabled for a Backup encryption option and hit Settings.

- Create a new encryption password or select a saved password if you don’t use a Key Management Service. Finally, proceed and hit the Finish & Run button at the Options step to save backup job settings and create a Microsoft 365 backup. Encrypted data is transferred and stored in a backup repository in the cloud.
Configuring Backup Copy to the Cloud
The common approach is to back up Microsoft 365 data to a local backup repository (on-premises) and then create a backup copy and send it to a public cloud, such as Amazon S3 or Azure Blob Storage. In both cases, you can enable backup encryption with the NAKIVO solution. The advantage of this method is that the local backup can be quickly created, and then it is copied to the cloud.
Let’s look at how to configure a backup copy of Microsoft 365 data to the cloud. In this example, we have a Microsoft 365 backup stored in an Onboard Backup Repository.
- Go to Data Protection, click + and hit Backup copy.

- Select the Microsoft 365 backup stored in a local backup repository. You can select multiple backups and select custom objects from backups. Hit Next to continue.

- Select a destination for the backup copy. We select a repository in Amazon S3.

- Configure schedule and retention options. You can enable backup immutability at this step.

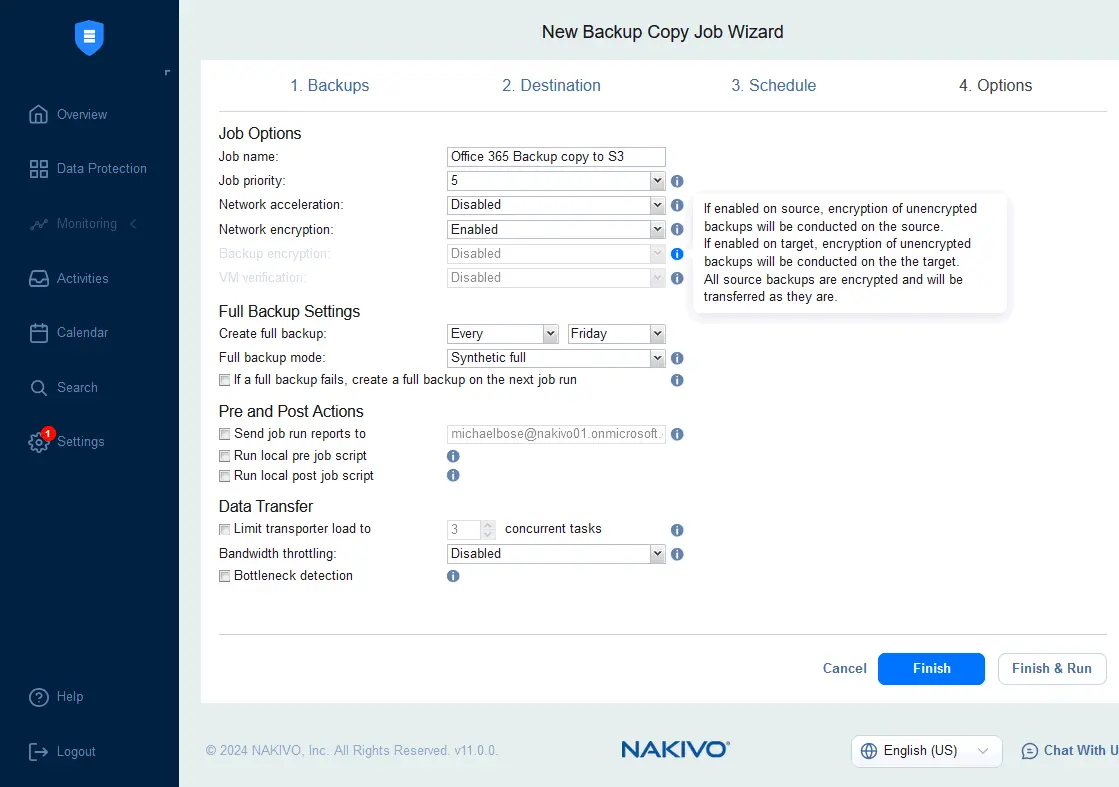
- Configure Microsoft 365 backup copy job options. If backup encryption is enabled for Microsoft 365 backup at the source (at the Options stage of the backup job), the backup copy is transferred in an encrypted state. If the backup job is configured without encryption, you can enable backup encryption at the Options step of the backup copy job wizard.
Click Finish & Run to save the settings and run the Microsoft 365 backup copy job to the cloud.
Conclusion
Microsoft 365 encryption is a measure that improves security when working with Office 365 services. Data is encrypted in transit and at rest for higher protection against unauthorized access. In addition to built-in encryption features, it is important to configure encryption for Microsoft 365 backups. NAKIVO Backup & Replication supports encryption for Microsoft 365 backups that can be stored in the cloud, such as Amazon S3, AWS EC2, Azure, etc. The NAKIVO solution encrypts backup data in transit and at rest. Download NAKIVO Backup & Replication and create encrypted Microsoft 365 backups in the cloud.




